Building with C2PA: A Developer's Primer
If you've ever signed a git commit, you already understand the philosophy behind C2PA. It's the same principle: cryptographically bind your identity to your work. The difference? Git signs code. C2PA signs reality.
At Silversparre, we asked ourselves a simple question: why should authenticating a photo be harder than authenticating a software release? The answer was clear—it shouldn't be. So we built a developer experience worthy of that principle.
What Happens Under the Hood
A C2PA manifest is essentially a JSON-LD document—structured, semantic, machine-readable. But here's where it gets interesting: this document doesn't just sit alongside your file. It's fused into the file itself, embedded in a special container called the JUMBF box (for JPEGs and other media formats).
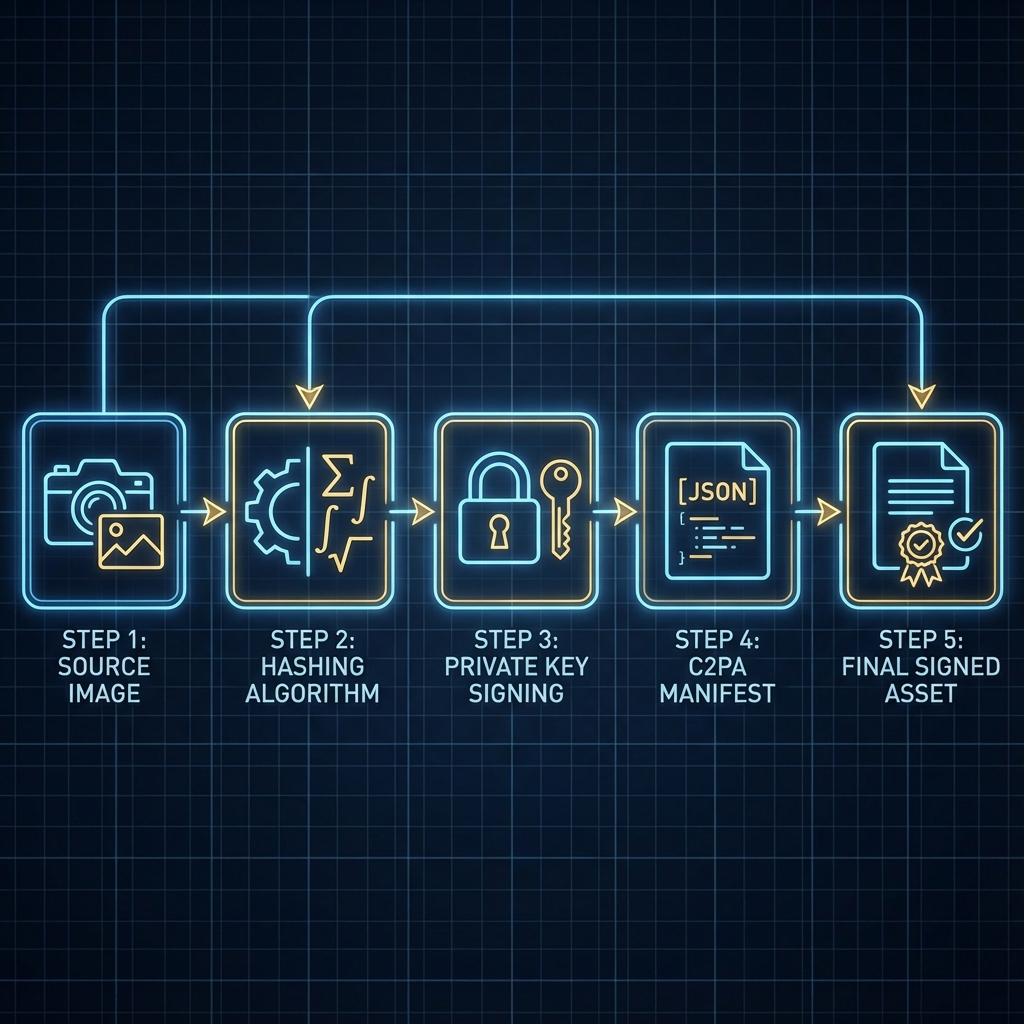
When the SDK processes your asset, it does three things in rapid succession:
- Hashes the assertion store — the structured claims you're making about the content (who created it, when, with what software).
- Creates a content binding — a cryptographic link to the actual media bytes, so even a single pixel change invalidates everything.
- Signs the whole package — using your private key, creating a signature that proves you made these claims, and no one has tampered with them since.
The result? A file that carries its own provenance. Share it anywhere—Twitter, email, USB drive—the credential travels with it.
The Performance Cost
Security always has a price, and usually, that price is latency. Cryptographic hashing is computationally expensive, especially for high-resolution 4K video. In our benchmarks, signing a 5MB image adds approximately 40-60ms of latency to the upload pipeline.
Is that perceptible? Barely. Does it matter? Absolutely. For real-time applications (like livestreaming), this header overhead accumulates. That's why our SDK supports lazy manifest injection, where the raw media stream flows immediately, and the detached signature arrives seconds later via a sidecar channel, stitched together by the player. We optimize for truth and speed.
Three Lines of Code
We've wrapped all this cryptographic machinery in an API so clean it feels almost anticlimactic. Here's all it takes to sign an image:
import { Vericord } from '@vericord/sdk';
const client = new Vericord({ apiKey: process.env.VERICORD_API_KEY });
// Sign and manifest the asset
const { signedUrl, manifest } = await client.assets.sign({
path: './breaking-news.jpg',
author: 'Reuters Field Desk',
assertions: [{ label: 'c2pa.actions', data: { action: 'c2pa.created' } }]
});
console.log(`Asset secured: ${signedUrl}`);That's it. Hashing, signing, ledger anchoring—all in one atomic operation. The function returns a URL to your now-verifiable file and the raw manifest for inspection or storage.
When Keys Go Missing
Here is the nightmare scenario: a major publisher's private key is stolen. Suddenly, an attacker can sign fake news with the cryptographic authority of a trusted newsroom. Cryptography is easy; key management is hard.

This is why Silversparre enforces short-lived certificates. Your signing keys rotate automatically every 24 hours. If a key is compromised, the blast radius is contained to a single day's content. We also maintain a real-time CRL (Certificate Revocation List) on the ledger. If we detect a breach, we kill the certificate chain instantly. Verified content stays verified; the attacker's "signed" fakes turn into digital dust.
A word on key hygiene: Your API key is the root of trust here. Store it in a secrets manager (AWS Secrets Manager, HashiCorp Vault). For bulletproof deployments, run signing operations through a Hardware Security Module (HSM)—the private key never leaves the hardware.
Build something that tells the truth. We'll help you prove it.